Active Directory - Restoring Deleted Objects
The various methods of object restore available for Active Directory
Introduction:
This post looks at how we can recover deleted objects in Active Directory Domain Services. It may be a rare occurrence that we delete something by accident, but when we do, what happens and how do we recover from these mistakes?
You may think recovering deleted objects is a piece of cake and while this is true in certain situations other methods are time-consuming and require several steps and some knowledge of AD replication.
So what methods do we have at our disposal to restore deleted objects?
Active Directory Recycle Bin (Easiest)
LDP.exe
NTDSUTIL.exe (Hardest)
We will go into each of these in detail, but first, let's see what happens to an item once it is deleted.
Deleting objects:
It's quite easy to delete an object in ADDS, right-click "Delete". When we delete an object it gets referred to as "tombstoned" and gets moved to a secret (not so secret) container in AD called "Deleted Objects". You can only see this container in certain AD-related applications/tools:
Active Directory Admin Centre (when the AD Recycle Bin is enabled)
ldp.exe
When Tombstoned the object is marked with an attribute "isDeleted" = TRUE. The object is then kept for a defined lifetime before it is permanently purged from the AD database. The lifetime is based on the Windows Server OS version but can be manually changed. See the table below for tombstone lifetimes:
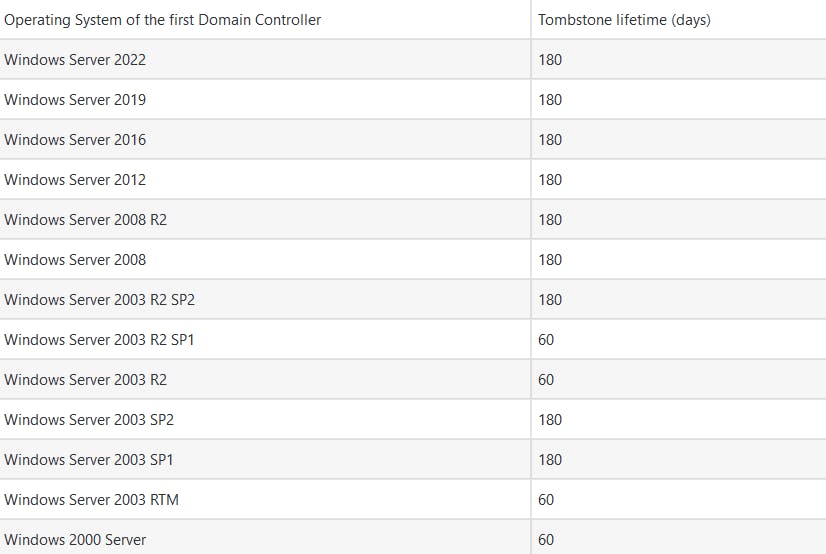
Once the lifetime of a deleted object is reached the AD garbage collection process will purge the object from AD. Garbage collection happens twice a day.
For this scenario, I have a user named "test3" that sits in the following directory location:
"cn=test3,ou=Users,ou=Switchitup,dc=Switchitup,dc=tech"
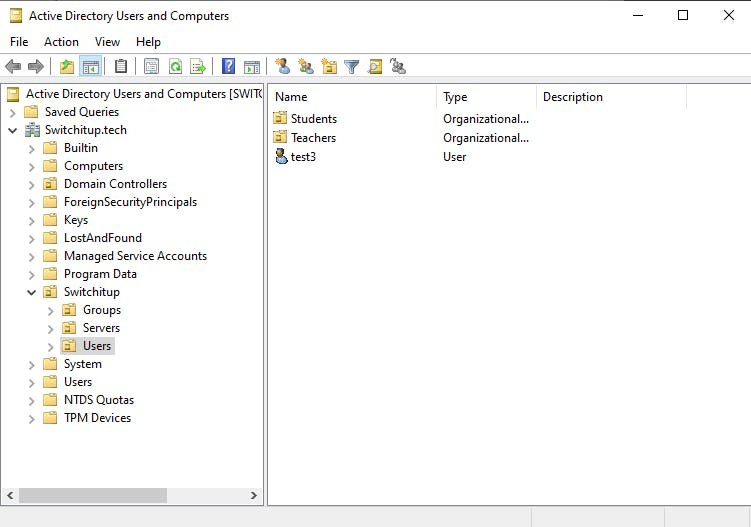
This poor individual will be the guinea pig for our restores.
Now we know how deleted objects are treated we also need to think about how AD replication can impact how we restore objects in a multi-domain controller environment
Active Directory Replication:
First of all, this only applies if you have multiple Domain Controllers in your infrastructure.
ADDS uses "multi-master" replication techniques to replicate the data between Domain Controllers. If you have a Domain Controller(DC) failure, ADDS continues to work amongst your "working" DCs and continues to replicate changes.
Two types of restores can be completed and used in different scenarios to control how restored objects are replicated. I like to think of each as "Pull" or "Push":
Non-authoritative (Pull) - Mostly used in a disaster situation where the whole system state needs to be restored. In this scenario, the restored database will normally be older than the current working Domain Controllers. When you bring the repaired DC online it will "pull" all the latest changes from the working DCs
Authoritative (Push) - Used more when you want to restore individual objects or OU's that got accidentally deleted. When objects are marked as "authoritative" the restored Objects will be "Pushed" to the working DCs
So now we know what happens to deleted items and how AD replicates between Domain Controllers let's now dive into the nitty gritty of how to restore objects:
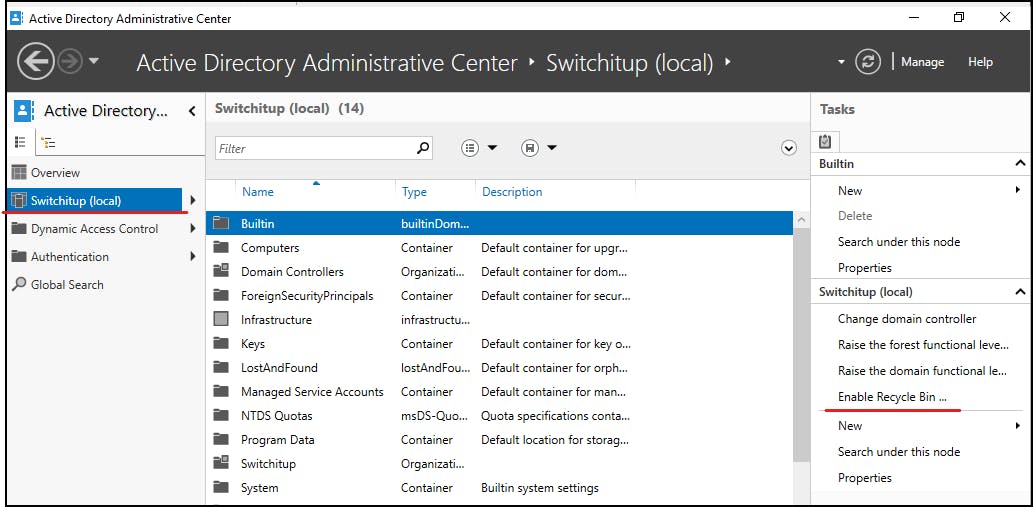
Active Directory Recycle Bin
This is available from 2008R2, you must also be at 2008R2 domain/forest functional levels and it must be turned on.
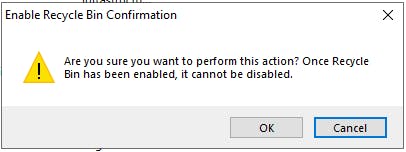
You will not be able to restore objects deleted before the recycle bin feature was turned on!
It also cannot be disabled once turned on, but there's no big deal breaker to this!
you will need to use the "Active Directory Administrative Centre"
The below screenshots show how to enable the feature:
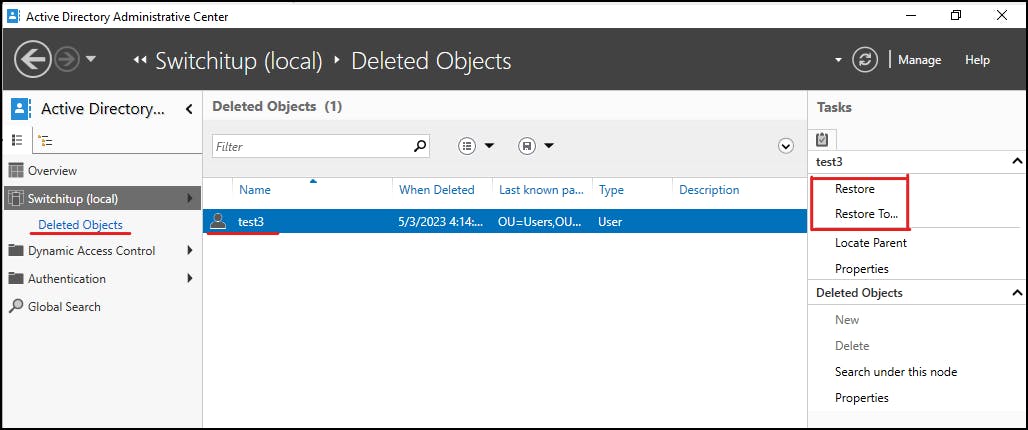
There will be a new "Deleted Objects" folder where all deleted objects will go when deleted. You can go in here to "restore" back to the OU location or "restore to" to select a new location to restore to in your directory.
LDP.exe
If your deleted object is still within your "Tombstoned" period you can use LDP.exe to restore the object. This only works when Active Directory Services are running, this won't work in DSRM mode.
search LDP and open up the application:

Select "Connection > Bind":
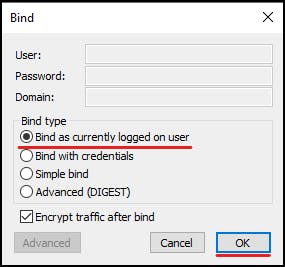
Make sure "Bind as currently logged on user" is selected and press "ok"
Now select "Options > Controls" :
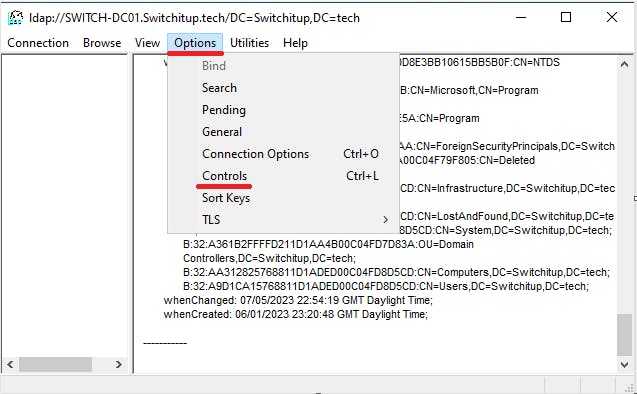
Now we need to select "Return deleted objects" from the "Load Predefined" drop down. then select "Ok"
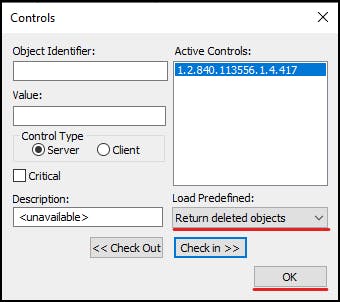
Now select "View > Tree"
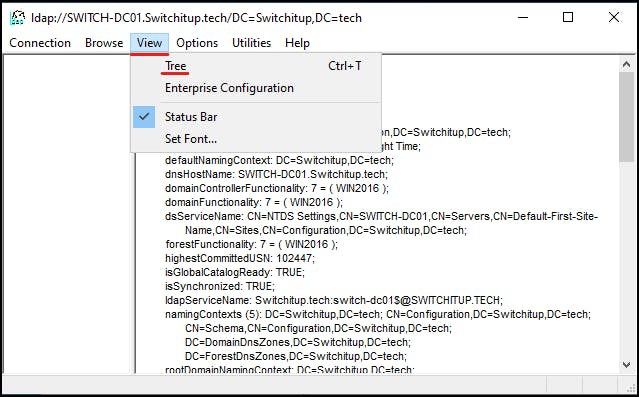
Type your top-level ADDS domain name in the following format:
Locate the deleted user in the "Deleted Objects" container. Double-click on the deleted user to populate the details in the right-hand pane. Notice "isDeleted" is TRUE and take note of the "lastKnownParent" path (location this object belonged to before deletion) (we are going to need this to restore the object).
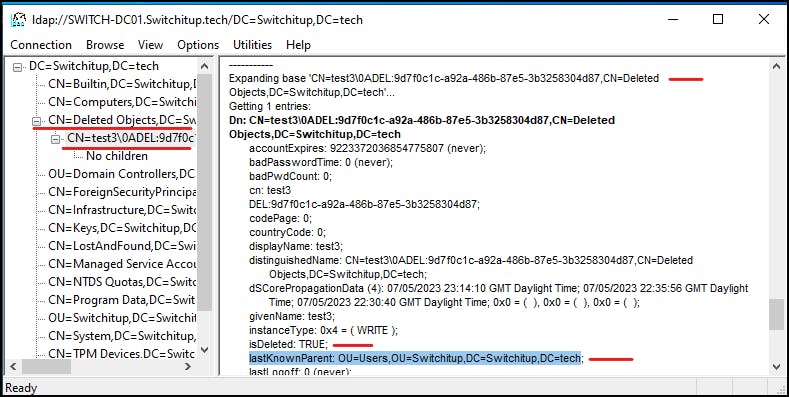
Right-click the user object and select "Modify"
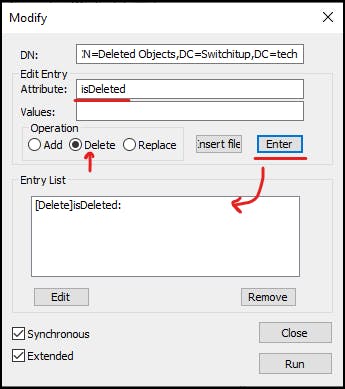
Edit Entry Attribute = isDeleted
Operation = "Deleted"
Press "Enter" to populate "Entry List"
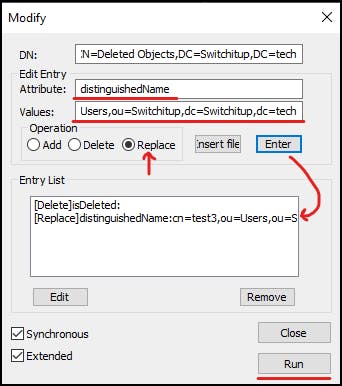
Edit Entry Attribute = distinguishedName
Values = CN=test3,OU=Users,OU=Switchitup,DC=Switchitup,DC=tech
Operation = "Replace"
Press "Enter" to populate the "Entry List"
Select "Run"
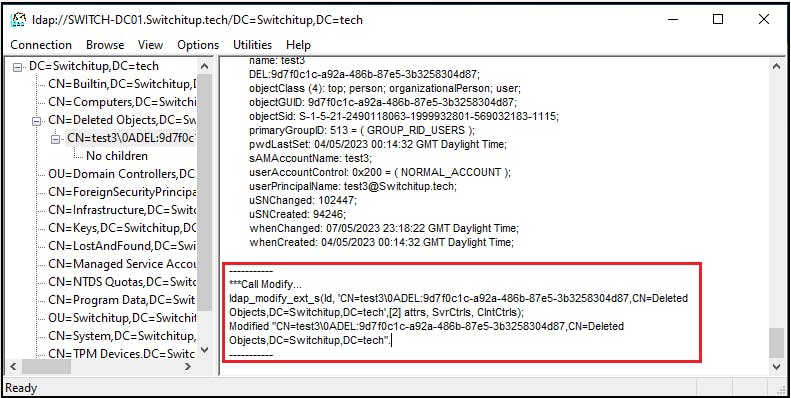
This will error if you haven't completed your values correctly and you will be shown the error in the right-hand pane. With all being correct it should look like the below:
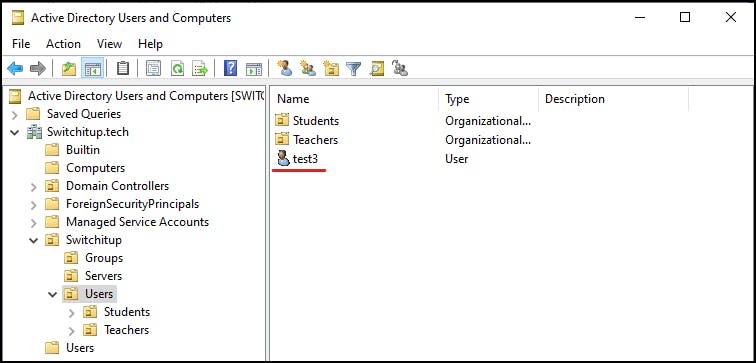
Let's check back into "Active Directory Users and Computers" and see if our user has returned. If you have this open already, hit the refresh button.
NTDSUTIL.exe
You can use NTDSUTIL to do Authoritative restores and other AD tasks such as defragment/compact the AD databases. It's also used to reset the DSRM password that's set when you first set up a Domain Controller.
To complete an Authoritative restore you will need to restore the "System State" of your DC to a time previous to the object deletion, for this we will use "Windows Server Backup". I will walk through the backup creation process and how to restore then we will use NTDSUTIL.exe to mark the deleted object for authoritative restore.
Restoring the System State will require a Restart of your server into "Directory Services Recovery Mode", you will then need to use "ntdsutil" to do the authoritative restore. Then force replication to your other Domain Controller(s) using "Active Directory Sites and Services".
Windows Backup - System State Backup
Firstly, we need to create a schedule that will backup the system state:
Let's see what's included in this type of backup:
System Registry
COM + Database
Certificate Services
Active Directory
SysVol
IIS Metabase
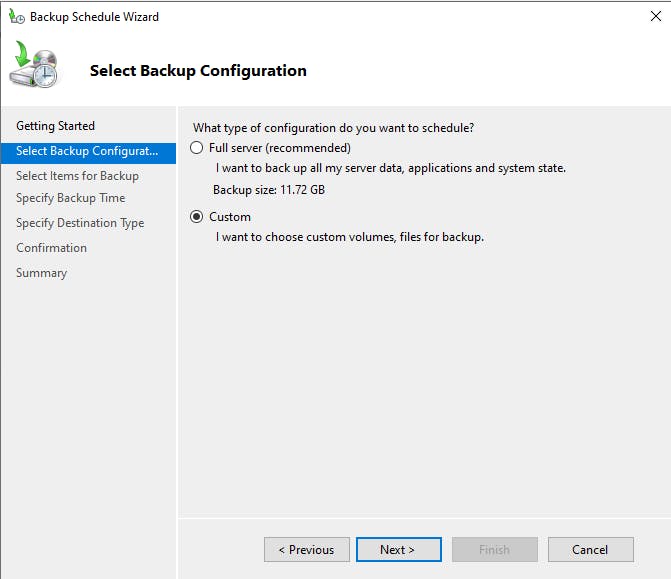
Select custom as we will select "System State" only.
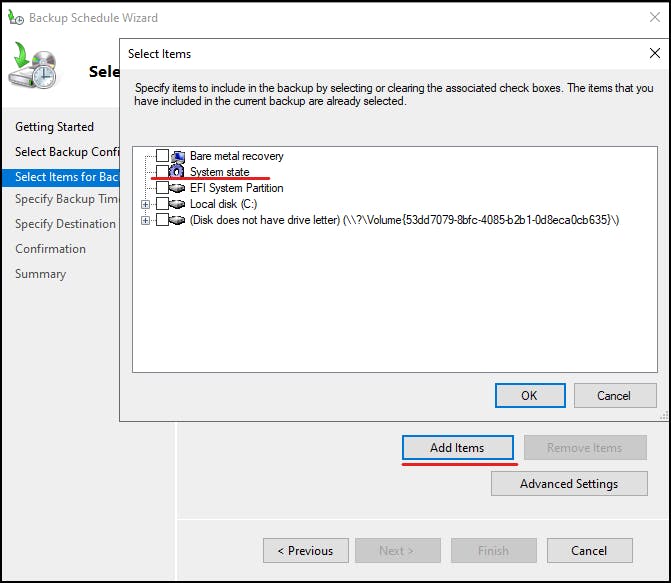
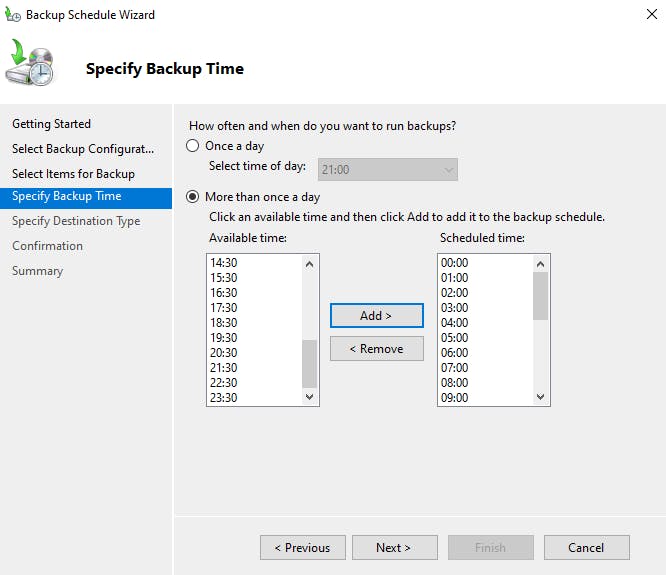
You can create a backup schedule, The more backups you have to restore from means more restore options. Select the relevant times you wish backups to run:
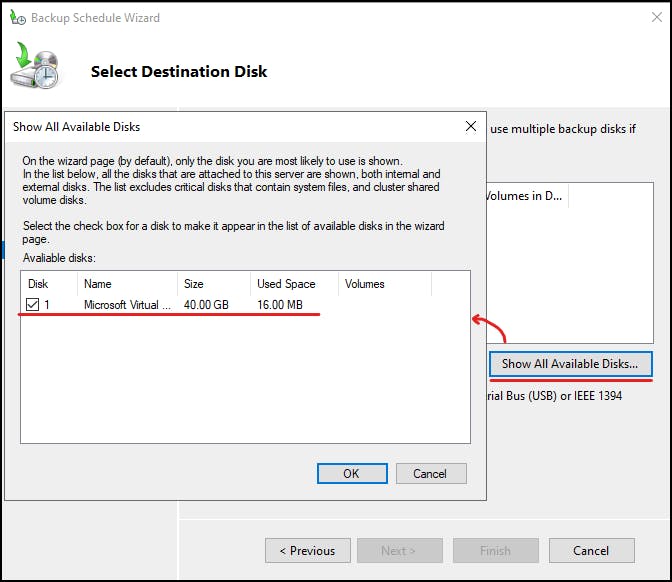
You can select any available disks, in my case I have attached a 40GB disk to my DC VM, I have only brought this disk ONLINE in the disk manager, not created a volume, Windows Backup will do this for you after you select the disk.
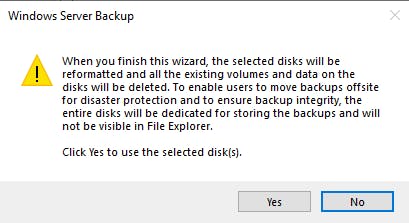
Finally, confirm your Backup Schedule:
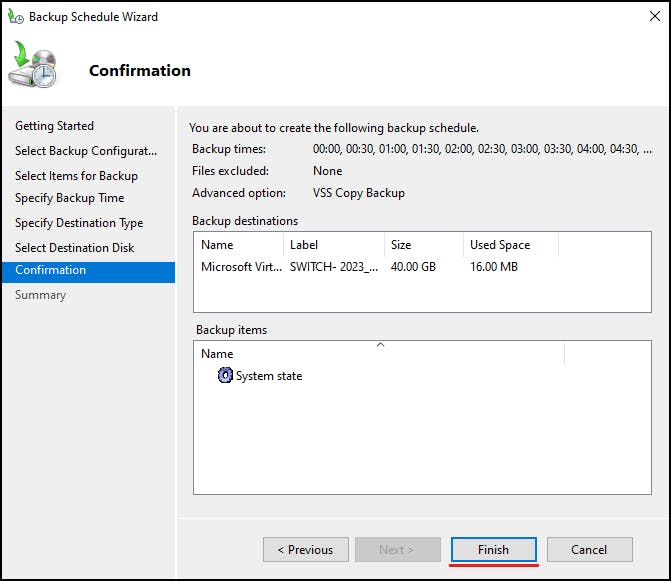
Directory Services Restore Mode
To complete the system state backup you will need to restart the DC into DSRM mode, then run system state restore to put the AD database back to a point before you deleted your objects.
To get into DSRM mode you will need the password you created when you built the DC, see the screenshot as a reminder below:
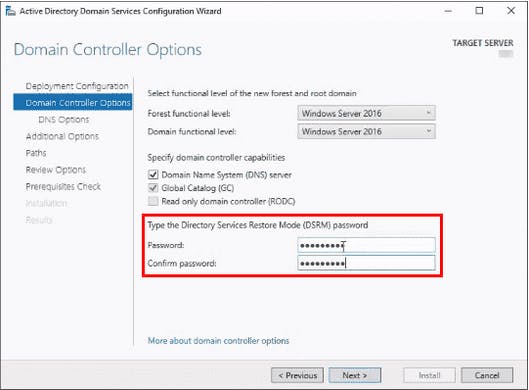
you can use ntdsutil.exe to reset this password if you have no recollection of it. The password reset process is as follows:
ntdsutil
#Password reset#
set dsrm password
enter your password of choice then re-type to confirm.
Now to reset into DSRM mode open the "System Configuration" tool, select the boot tab, make sure "Safe Boot" is selected and "Active Directory Repair":
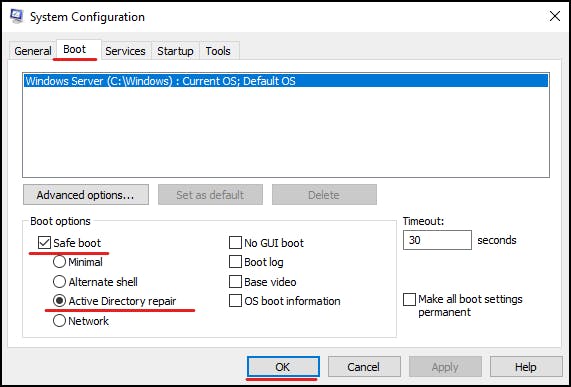
This will force a reboot.
To access DSRM on reboot you will need to log in as .\administrator using the DSRM password as you will not be connected to the domain. You will be booted into Safe Mode.
Now we can recover the system state using Windows Backup Tool.
Windows Backup - System State Recover
From the Windows Backup MMC, select "Recover" from the right-hand pane:
We want to backup from this DC:
Select your desired backup date and time restore point, to restore the system state to:
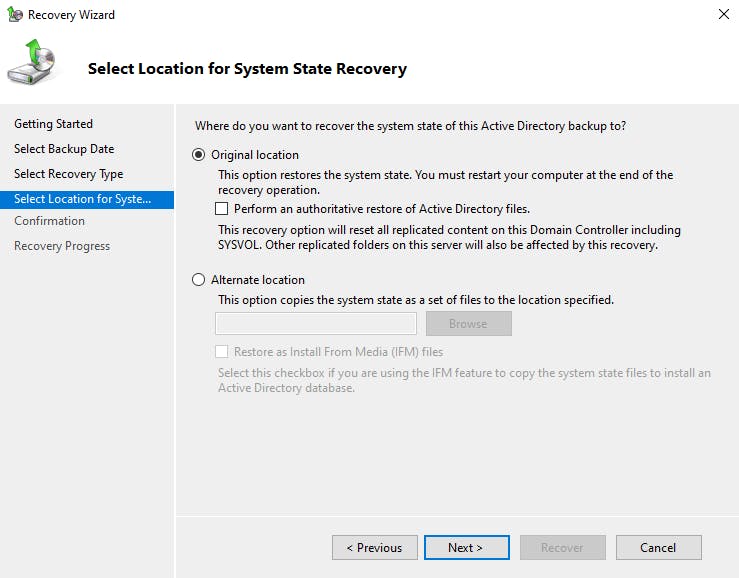
Select System State:
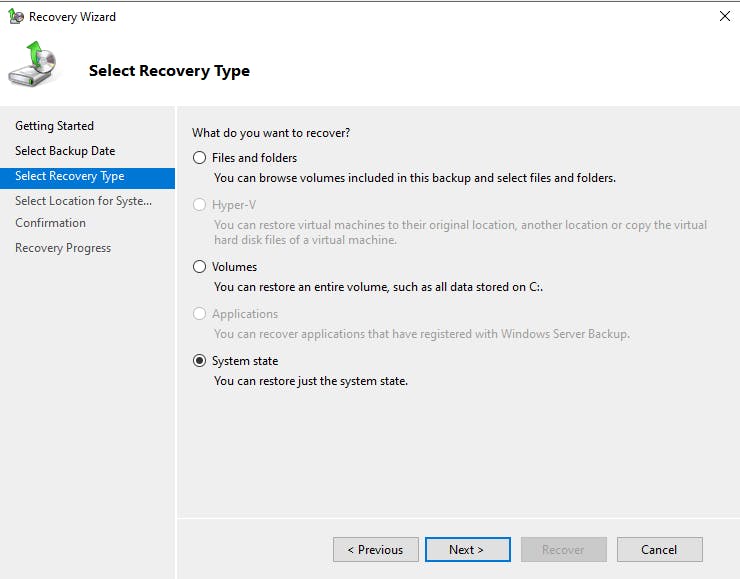
Notice on this screen we can make the entire Active Directory Restore "Authoritative". This would mean this system state would be pushed to all member DCs which could be catastrophic and is not what we need right now. So just select the original location, this will be a non-authoritative restore, however, we will use ntdsutil to make the deleted objects we wish to restore authoritative so only these are pushed out to member DC's.
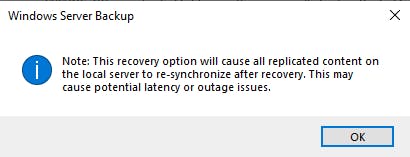
Hit "recover" to start the system state restore
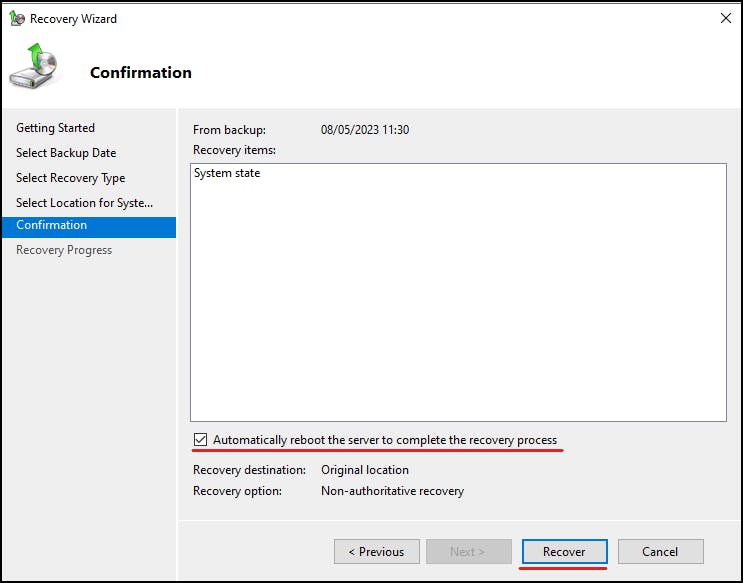
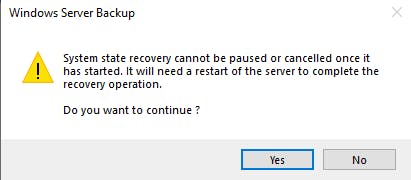
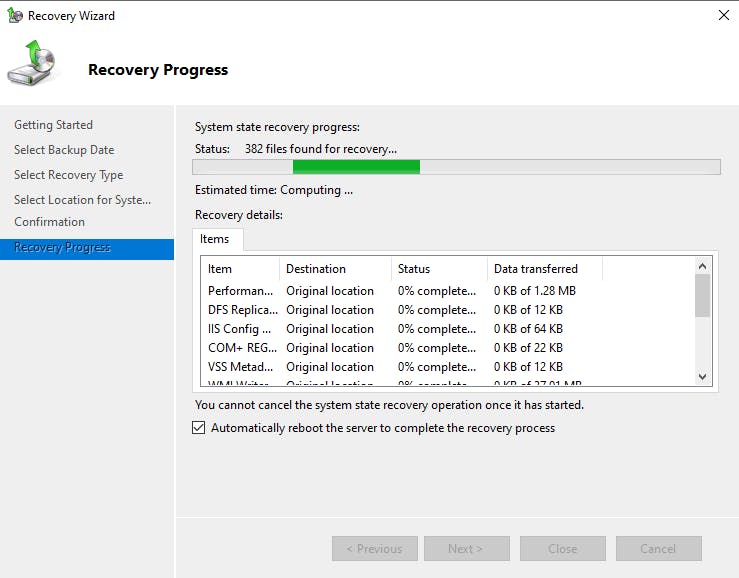
On completion, you will need to restart to finish the restore process, if you have not selected automatic restart.
Authoritative Restore
we can now make the authoritative restores in NTDSUTIL. You can access this from the command prompt (CMD) type: "ntdsutil"
? will bring up the help menu:
#run ntdsutil.exe#
ntdsutil
#activate ntds instance#
activate instance ntds
#authoritative restore#
authoritative restore
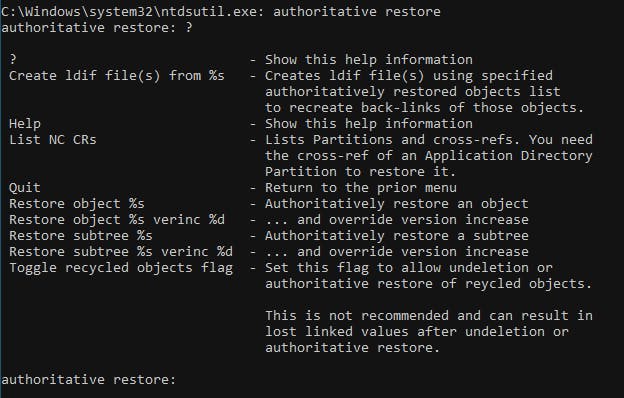
restore objects "CN=test3,OU=Users,OU=Switchitup,DC=Switchitup,DC=tech"
Once restored we now need to go back into the "System Configuration" tool and turn off "Safe boot" so we can return to normal login.
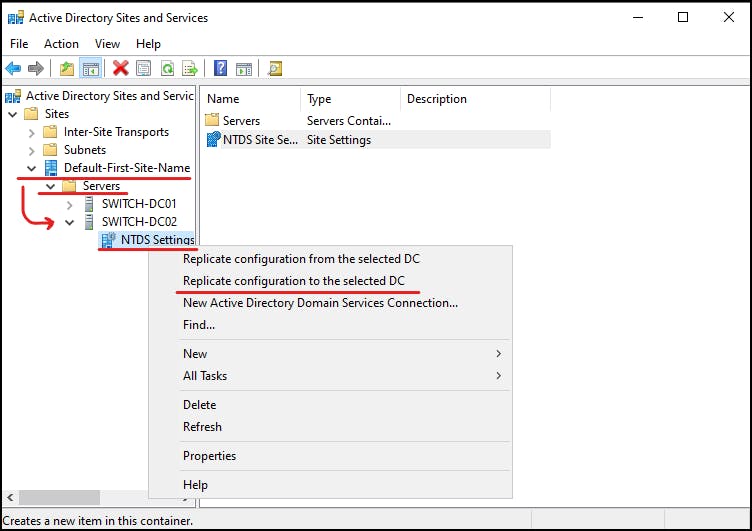
Replicate the Changes
Once you have logged back into your domain controller we need to replicate the changes to our other DCs, we can do this in "Active Directory Sites and Services":
Summary:
As you can see it makes sense to enable the AD Recycle Bin as this is the quickest and hassle-free method unless, of course, you end up corrupting your AD database then you will need to restore the system state.
Bear in mind the two types of restores and how they work as this will have an impact on how you may want or need to restore in certain scenarios.

